Two-factor authentication (2FA) is one of the best ways to add an extra layer of security to your online accounts. That secret code prevents a whole lot of hacking attempts, and it’s great that many people are using it these days. However, how you get that code is extremely important. If you have been using SMS as I did for the longest time, I have a huge favor to ask you — please stop.
Whether it’s Facebook, Amazon, or PayPal, many of us choose to use SMS for two-factor authentication. But SMS was designed with zero security in mind, and that is why it’s the weakest method of getting that important code. You can even choose a different authentication factor other than SMS codes. Let’s talk about it.
SMS is the simplest way to receive your two-factor authentication code
But simplicity can mean that something is lacking
I get the appeal behind using SMS as your preferred 2FA method — it’s unparalleled convenience. There’s no app to download, no settings to manage, and no technical knowledge required. You just provide your phone number, and the code comes to you on a device you always have near you. It doesn’t require an internet connection, and even an old non-smartphone can receive an SMS.
Despite its convenience, usefulness, and universality, SMS has some security gaps. Let me just cover the two biggest ones that should keep you up at night.
SMS uses an outdated transmission protocol
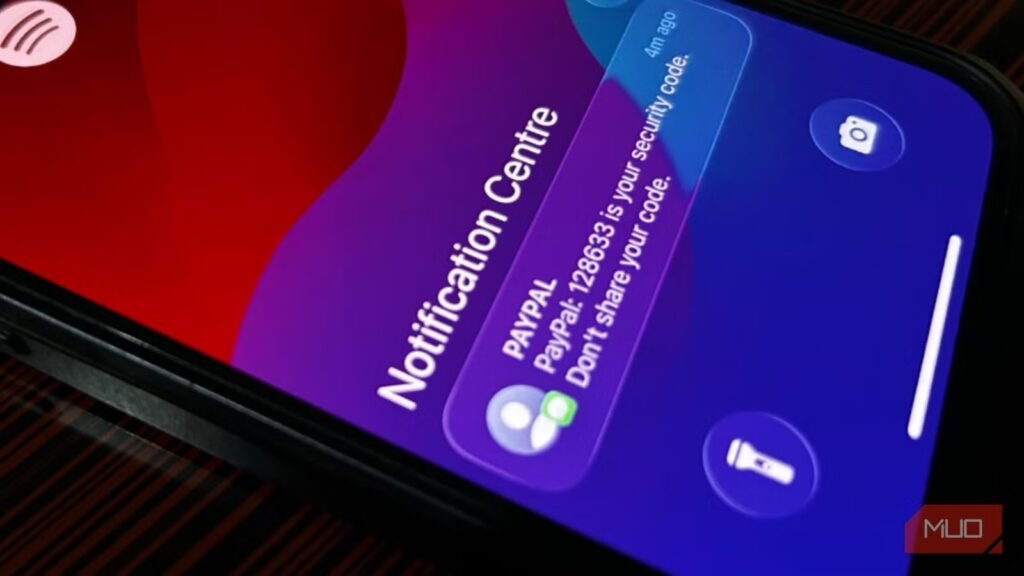
Screenshot by author, Spencer Abel. No attribution needed. Credit: Spencer Abel/MakeUseOf
The biggest problem with using SMS is that the underlying technology is outdated. It just cannot handle modern security needs because it uses an old transmission protocol called Signaling System No. 7 (SS7), developed in the late 1970s and 1980s. It’s easier to exploit because it was developed at a time when access was limited and everyone using it was trustworthy.
The main problem with SS7 is the lack of cryptographic authentication. To put it simply, the protocol assumes any message in its signaling network is coming from a legitimate source, meaning a hacker who gains access to it — usually through a poorly secured carrier — can transmit malicious commands that track, impersonate, and intercept messages.
It gets worse. The SS7 protocol lacks the end-to-end encryption we take for granted in apps like WhatsApp and iMessage. SMS messages are transmitted as plain text, meaning hackers can intercept messages with the 2FA code and easily read them since they’re not encrypted.
Other than seeing the content of the message, the hackers also have access to the metadata. That means they can see other information like phone numbers, location, and device information attached to the messages.
SIM swapping is a growing threat
These days, hackers don’t even need to gain access to the signaling network to hack your account. They can exploit one of the weakest links in any security chain — humans. Hackers can use phishing to trick your carrier into transferring your phone number to a SIM card they own. Afterward, they can receive two-factor authentication codes meant for you, allowing them to access your accounts.
Related
eSIMs Can Be Hacked, but I Keep Mine Safe With These Tips
A few simple steps a day keep the hackers and cybercriminals away.
How big a threat is SIM swapping? Well, according to a TransUnion report, around 27% of telecommunications executives in the US consider SIM swapping to be the biggest emerging threat in telecommunication fraud. However, SIM swapping actually ranked second, with synthetic identity fraud (30%) taking first place and device theft (20%) coming in third.
What you can use for two-factor authentication instead of SMS
Other factors of authentication besides SMS
Another problem with SMS that I find annoying, rather than a security flaw, is that it can fail you when you need it most. I remember trying to log into my Amazon account on a different device, and when I tried to send the code via SMS, it never came. Sometimes the code arrives after resending, but after repeated failures, I decided that SMS is not reliable for receiving 2FA codes. I’ve experienced similar issues with PayPal and Payoneer.
Related
Here’s the One Thing Hackers Hope You Never Do With Your Email
This single setting can save your email from being hacked.
Here are safer and more reliable alternatives to SMS for two-factor authentication:
- Authenticator apps: You can use Google Authenticator, Microsoft Authenticator, Authy, or any other authenticator apps that generate a TOTP (time-based one-time password). This is a temporary, one-time use code — many popular accounts allow you to link authenticator apps to them. These apps reset the code every 30 seconds and work even without internet access. The codes are safe since they’re generated locally instead of being sent over a network.
- Passkeys: You can also use a passkey, which is like a digital credential that’s stored on your device (e.g., phone or computer). When logging in to an account, the server sends your device a challenge to sign using a private key stored locally. When signed, the server verifies the signature using a public key, giving you access when everything checks out. So, unless the hacker physically steals your phone and bypasses the security (e.g., passcode, fingerprint, or facial recognition), they aren’t getting into that account.
- Security keys: You can also turn a USB into a security key (e.g., YubiKey). This works in the same way as a passkey, but the challenge is signed with the security key instead. Again, someone would have to get a hold of the security key physically to be able to hack your accounts. Physically obtaining the key is very risky, which is why hackers overwhelmingly rely on remote attacks.
Of course, there are more methods than this. These are just the ones that are relatively easier to set up and offer way more security than SMS.
SMS provides a false sense of security
Using SMS for 2FA makes people complacent because they actually think they’re protected. It works, and that’s all they need to know. However, it’s a huge security risk to rely on technology that hasn’t evolved since the 1970s. We are in the digital age, where threats are rapidly evolving, widening the security gaps of this outdated technology further. It’s time to switch to something better.